Zero-Day Exploit in Internet Shortcuts: What You Need to Know about CVE-2024-38112
The APT group known as Void Banshee has been conducting spear phishing campaigns at a near global level for several months. The group has been making use of a zero-day exploit found in the rendering engine for Internet Explorer, known as Trident. The final payload for the attack is the Atlantida Stealer malware. This malware steals system information and can capture the infected machine’s screen, before exfiltrating data via a C2 (Command and Control) channel back to the attacker.
The Bait
The attack relies on the vulnerability CVE-2024-38112 and attempts to trick users into downloading and executing malicious files. The attack relies on a user clicking on a link distributed by means of social media or email. The malicious file is contained within a zip archive and is disguised as a PDF. The real file extension is actually URL, which is an extension used to provide users with a shortcut to open a web browser to a specific address.
When the user opens the “PDF” they are instead navigating to the URL shown below. The file exploits the use of mhtml and x-usc to force the user to open the URL in Internet Explorer 11 rather than a modern browser such as Chrome or Edge. As you can see below, the icon has been manually altered to show the icon for Microsoft Edge (the default PDF file viewer on most machines).
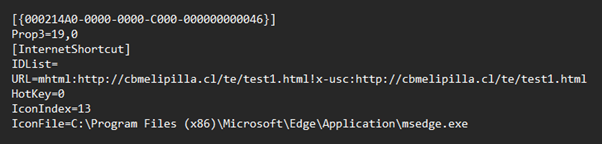
The Tackle
Within the request headers of the website is a GET instruction to download a file. The user is presented with a prompt showing the file appearing as a PDF with the option to open it. The user, expecting a PDF when they opened the file originally, then clicks ‘Open’. The file that has actually been executed is a malicious HTA file. The exploit makes use of a bug where the full file name is obscured, with Windows omitting the true file extension.
So, what’s so bad about HTA files? The file type refers to HTML Applications. These files are run by Microsoft HTML Application host – a native, signed binary that exists in all Windows installations. HTA files are dangerous as they are able to execute arbitrary Windows Script Host code such as VBScript and JScript.
This is the primary post exploit attack vector. Once the HTA file has been executed, the host is then instructed to download the intended malware — the Atlantida Stealer — and establish a C2 (Command and Control) channel with the attacker.
Am I Affected?
For organisations running Windows 11 on fleet laptops, you would expect Internet Explorer 11 to be removed by default. In reality, IE11 is still a core component of the operating system and is able to be called when needed. Running any website in Internet Explorer mode inside of Microsoft Edge still runs IE11 in the background. Additionally, MSHTA is one of the known applications that can bypass common application control solutions, as the VBScript and JScript is run in-line. This means that the vulnerability affects all machines running Windows 10/11 – even those with Internet Explorer disabled.
Fortunately, Microsoft released a patch for this exploit as part of the July 9 monthly update release cycle. Unfortunately, there is evidence that APT Void Banshee has been exploiting CVE-2024-38112 as early as May 2024. Additionally, the patch does not include any changes for Internet Explorer 11, which ceased support in June 2022, and was “permanently disabled” in February 2023. The patch instead simply removes the association between MHTML and Internet Explorer 11 from the Operating System. If the URL file is executed on a patched system, the user is presented with a generic prompt.
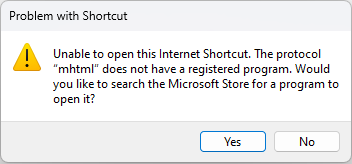
How could this have been prevented?
As this vulnerability affects all Windows 10/11 machines and MSHTA is able to bypass Windows Defender Application Control to run inline scripts, the only solution is to block MSHTA entirely or prevent machines from running unauthorised HTA files if the organisation requires MSHTA for critical business functions. This is a key component of the ASD’s Essential Eight Framework Application Control pillar. Adhering to the controls within this pillar will help to prevent future attacks that make use of MSHTA. For more information about the Essential Eight Framework, read our article on the topic here.
Organisations can use WDAC or a 3rd party application control solution to block MSHTA from running. Ensure that the definition is based on the hash of mshta.exe as adversaries have been known to change the filename and location of the binary to overcome basic detection.
Most importantly, ensure that all critical systems are updated with the latest patches from Microsoft, and always be wary of unexpected emails and files. Conduct regular phishing simulation exercises to ensure that your workforce is responding to potential threats appropriately.
Why Frame Secure?
Addressing cybersecurity vulnerabilities is paramount for safeguarding your organisation’s assets and reputation. Frame offers tailored solutions to effectively mitigate these risks.
We provide comprehensive assessments to evaluate your organization’s cybersecurity posture, aligning with industry standards and regulations. Our accredited experts, certified by leading vendors such as Microsoft, Cisco, and VMware, deliver fast and reliable assessments to ensure that your organisation meets the highest standards of cybersecurity.
Don’t wait until it’s too late. Take proactive steps to enhance your cybersecurity posture with Frame’s tailored solutions and expertise. Secure your organisation’s future today.

